If you’re asking yourself “do I need an SSL certificate?” the answer is yes, and here’s why…
If you have a website, even if it is a basic one, you’re likely facing the question of whether you need an SSL certificate. With all of the other costs piling up, you might be tempted to do away with having one more additional bill. But before you decide not to get one, ask yourself a few important questions first:
- Why do I need an SSL certificate?
- What is the risk of not having an SSL certificate?
- What happens if I don’t have an SSL certificate?
We’ll answer those questions and explore the reasons why you need an SSL certificate on your organization’s website. But first, let’s start by talking about what an SSL certificate is.
What Is an SSL Certificate?
An SSL certificate, or more specifically a TLS certificate, is a digital file that you use to secure and identify your website as legitimate. What it does is tie your organization’s cryptographic key to your brand so no one else can use it. It’s a crucial element of having a secure website and is what makes the secure padlock appear in your website’s URL bar. It’s also what makes the “HTTPS” appear at the beginning of the URL as well.
HTTPS is a secure protocol, whereas HTTP is an insecure one. And, as you can imagine, using a secure protocol is always better than using an insecure one when it comes to transmitting personal or otherwise sensitive data.
For example, here’s how it looks on our website when we use an SSL/TLS certificate:


In the screenshot example above, you’ll notice that there’s a padlock in front of our website’s domain. This padlock indicates that the website is using a secure, encrypted connection. This is an indication that the site is using an SSL/TLS certificate. So, to answer the question “do I need an SSL certificate?” The answer is unequivocally “yes!”
When users connect to websites without SSL/TLS certificates via the insecure HTTP protocol, it means their information transmits through insecure connections (HTTP). Essentially, their info is traveling across the internet in plaintext (i.e., readable) format that cybercriminals can intercept, read, and modify in transit. But when they connect with websites that use SSL/TLS certificates (which enables HTTPS), their information is encrypted, meaning that it’s no longer readable and appears like gibberish to anyone who tries to intercept it.
In the most basic sense, this certificate enables you to use encryption to protect the data that transmits between your customers’ clients (web browsers) and your server. It does this by allowing your server to identify itself as being legitimate to clients.
In a more technical sense, what this certificate does is provide instructions and authentication information your web server can use to establish secure, encrypted connections with clients. Historically, all of this used to occur via the secure sockets layer (SSL) protocol. Nowadays, however, the TLS protocol (which stands for transport layer security) is the go-to secure protocol. Hence why we said earlier that they’re really TLS certificates. (The industry is slow to update its lingo, though, so people still commonly call them SSL certificates.)
What Are the Risks of Not Having an SSL Certificate?
More than $3.5 billion. That’s what the FBI’s Internet Crime Complaint Center (IC3) says was reported as being lost to cybercrimes in 2019 alone. According to this report, the IC3 received a total of 467,361 cybercrime-related complaints that year — most of which were related to phishing, non-payment/non-delivery, and personal data breaches.
Needless to say, this underscores the importance of data security and safety. And SSL/TLS certificates are just one of the crucial cogs in the complex data security machine.
By not installing an SSL certificate on your website, you’re leaving your website and your customers open to an assortment of risks:
- Man in the middle attacks. We’ve already touched on this, but a MitM attack occurs when a cybercriminal intercepts the data that transmits between users’ web clients and your server.
- Data leaks. Data leaks are another concern when you’re not sending or receiving data via a secure, encrypted connection.
- Phishing attacks. When you don’t use an SSL/TLS certificate on your site, you’re not authenticating yourself. This leaves your brand open to being used in phishing attacks because users can’t easily identify whether an imposter’s phishing website is real or fake.
- Your site will be distrusted by browsers. Everyone wants their website to appear in the top search results of different search engines. But did you know that not using an SSL/TLS certificate on your website can actually make it so that the major browsers (Chrome, Firefox, Safari, etc.) won’t trust your site? We’ll speak more to that momentarily.
- Noncompliance issues. You’ll read more about this shortly, but not having an SSL/TLS certificate on your website can lead to noncompliance issues with a variety of industry regulations, including HIPAA, GDPR, CCPA, PCI DSS, and FIPS.
- Brand and reputational damage. As you can imagine, all of these things may cause customers to lose faith and trust in your brand. This can result in lost business and affect your bottom line.
How Is Google Promoting the Use of SSL Certificates?
We cannot emphasize enough the importance of having an SSL certificate. It is evident when tech giants like Google, Apple and Mozilla have made it mandatory for secure sites that want to rank on their browsers to have one. In 2014, Google declared that it considers an SSL certificate among one of its ranking factors. Since 2017, Google labels sites that collect login data or credit card details without the use of an SSL certificate as “Not Secure” in the address bar of Chrome. They do the same with websites whose SSL/TLS certificates have expired.
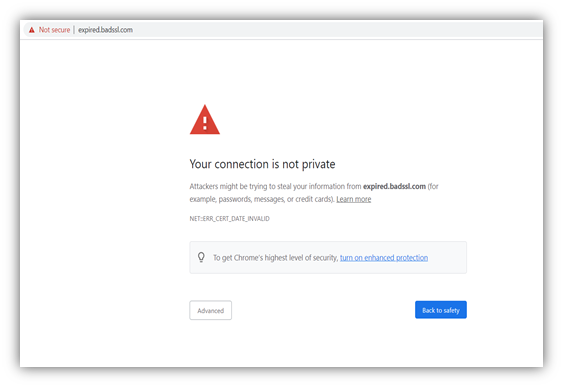

What happens if I don’t have an SSL certificate on my site? You get your answer in this picture. The website will display the “Not Secure” message in the browser’s URL bar to all your site visitors. This may drive traffic away from your site and straight into the arms of your competitors.
Google went a step further in 2018 when it began marking all sites without SSL certificates as “Not Secure” regardless of whether they collect user data. Slowly, they’ve been rolling out measures to ensure that sites that have SSL certificates will no longer have the green padlock. However, the sites without an SSL certificate will be marked in red on the address bar, rating them as “Not Secure.”
Consequences of Not Having an SSL Certificate in Terms of Compliance
Not only Google, but other important industry regulatory entities have also made it compulsory to have SSL certificates for websites that handle credit card data. One such example is the Payment Card Industry Security Standards Council (PCI SSC).
PCI SSC designs and manages security standards called PCI DSS (Payment Control Industry Data Security Standards) to provide airtight security for credit card transactions. What PCI DSS does is ensure that the collection, storage, processing, and transmission of credit card details of the customers are done in a safe environment. Companies that collect and process customers’ credit card information must comply with PCI DSS. Failure to do so can lead to dire consequences, including heavy fines and other penalties from Visa, Mastercard, Citibank, Chase, and American Express.
Other Effects of Not Having SSL Certificate on Your Business’s Website
While cyber awareness is slowing growing among consumers, the Fiserv 2019 Cybersecurity Awareness Insights Study reports that “a surprising number of U.S. consumers have little awareness of how to defend themselves against a cyberattack.” However, they can still read warning signs, and the ones from browsers screaming “Not Secure” are sure to catch their attention. Also, even the most ignorant of them will recognize the red warning in the address bar means “stop”.
While 44% of the survey respondents say they want governments and businesses to do more about cyber security, 59% say they’re bothered by the inconvenience created by advanced security measures. Cyber security is a partnership between businesses, citizens, and the government to defend themselves against cybercriminals.
Nowadays, consumers have numerous options to choose from. When they find out that your website is not secure, they’re more likely to close out of your website to find one that doesn’t display any scary warning messages. As a result, you might lose genuine customers if you do not have an SSL certificate to prove your organizational identity and generate trust. Far from buying anything from your website and sharing important information like payment details, they will avoid sharing their email addresses to stay safe.
While customers believe they are becoming more knowledgeable about security, cybercriminals are also adapting and finding new ways to trick them. These bad guys continually develop different new ways to hack websites with malicious intent to defraud people and businesses and to cause general mayhem. An SSL certificate not only helps you to gain the trust of your customers, but it also helps to guard their information from man-in-the-middle (MitM) attacks.
Hence, although an SSL certificate is not technically “mandatory” for a website, per se, not having one will make it almost impossible for website owners to be successful online. Neither your customers nor any banks will be able to trust your brand. We can say that SSL certificates are the need of the hour and they will be made mandatory in the foreseeable future.
Do I Need an SSL Certificate?
If you’re still not convinced and are asking yourself “why do I need an SSL certificate?” let us conclude this article by quickly summarizing the reasons to persuade you.
- If you do not have an SSL certificate, your site’s search ranking will plummet on Google Chrome. This will make it virtually impossible for customers to reach your website since most customers don’t go beyond the first page of Google search results. In fact, the Search Engine Journal reports that the second page of Google search results has less than a 1% click-through rate (CTR).
- All of the major browsers will not trust your site, and some (e.g., Google Chrome) will punish your site by decreasing its search engine ranking for your site.
- Not having an SSL certificate will make your website appear as “Not Secure” in the address bar. This will turn red as Chrome rolls out the transition in some time. This will alert the visitors that your website cannot be trusted and may result in decreased web traffic.
- If you ask for the credit card details of the customers without an SSL certificate, you’ll be non-compliant with PCI DSS and are likely to face heavy fines and penalties.
- Not using an SSL/TLS certificate can leave you noncompliant with other industry regulations as well.
- Criminals will have an open field to attack your website and steal your customers’ personal data. This can result in a loss of trust and even potential lawsuits in the future.
The above points prove the absolute necessity of having an SSL certificate on your website. At the end of the day, your return on investment (ROI) will be much more with the SSL certificate than without it.
Purchase Your SSL Certificate
There are many different types of SSL Certificates available for you to choose from. To find the one that suits your needs, you can click the button below.