How cybercriminals strip use this form of Man-in-the-Middle attack and what you can do to stop them
SSL stripping attacks make sense on an intuitive level as soon as you hear the name. But, on a technical level, most people have no idea what’s actually happening or how it works.
Granted, some people are completely happy to live their entire lives without finding an answer to that question. We call those people normal and well-adjusted. But, if you’re reading this, that clearly isn’t you. You’re like us — your mind yearns to rent space to obscure facts and explanations. We appreciate that mentality.
SSL stripping, as the name implies, is an attack that uses the SSLStrip tool or related techniques to strip away the protection provided by the SSL/TLS protocol and HTTPS. It’s a form of Man-in-the-Middle attack (MitM) that takes advantage of the TLS protocol and the way it begins connections. To understand everything, we’re going to need to start with HTTPS and MitM.
HTTPS and the Man in the Middle
When the worldwide web was first conceived, it wasn’t intended for commerce or vital services. It was a way for the government and academia to share information. This didn’t require much security.
When the internet was commercialized, security and privacy became key considerations in an “oh $#!%, we need to do something about this” kind of way. The creation of the secure sockets layer (SSL) protocol was the first attempt at an answer. It made connections via a secure channel, port 443, and layered encryption over connections at the application level. This was known as HTTP over SSL or HTTPS.
The Move from SSL to TLS
But SSL was flawed and was quickly found to be vulnerable. SSL 3.0 was replaced with transport layer security (TLS) 1.0 in 1999. The key difference was that TLS began connections with a hello via an insecure channel before being redirected to a secure one. Both use port 443 and encrypt HTTP connections. But the genesis of those connections differed.
And that’s where SSL stripping comes in. But before we can get there, let’s discuss the man in the middle.
Where Man in the Middle and SSL Stripping Intersect
When you connect to a website — or, really, any network on the internet — your connection has to be routed through dozens of other points on its way to its destination. It’s not a 1:1 type of thing. If you’re not using encryption/HTTPS, all the data you’re transmitting over that connection passes through each one of those points in plaintext.
That means anyone that is eavesdropping at one of those points — which aren’t all secure — can effectively intercept, read, and even manipulate everything being communicated. The answer to this has historically been to encrypt the connection so even if someone is eavesdropping the data is in ciphertext and unreadable to the attacker.
What does all of this have to do with SSL stripping, you may wonder? SSL stripping is a workaround for that encryption.
What is SSL Stripping?
Ok, remember we just discussed how TLS begins with an insecure hello (just like my dating life) before it’s redirected to a secure channel. If a Man-in-the-Middle attacker can redirect the client to an HTTP version of the website, it can steal information and manipulate the connection.
There are several ways this can be done. The easiest is probably to set up a spoof Wi-Fi network in a public setting and attack the people who long onto it. You can also compromise a point somewhere in the middle of the connection.
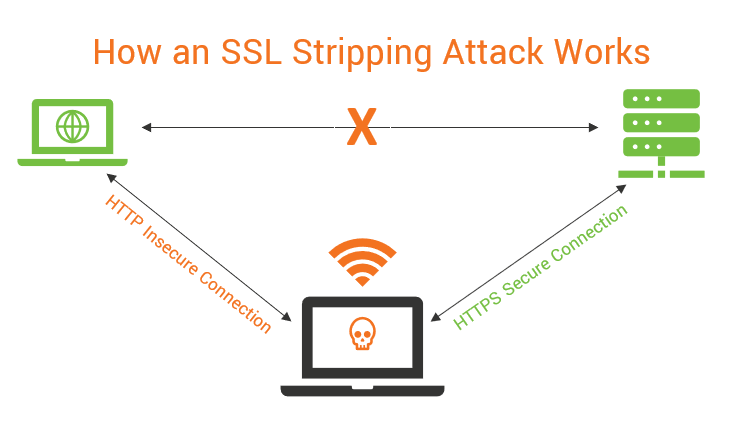

Because that initial hello and HTTP redirection request is unencrypted, a MITM can alter it and send the user to an insecure version of the page. Keep in mind, however, that when you install SSL, you’re essentially creating a duplicate of your website with HTTPS URLs. Those original HTTP URLs still exist, though. Usually, you use 301 or 302 redirects to ensure users can’t reach the HTTP site, but if an attacker can manipulate the redirect, they can still send the user to that page.
Now the user is still on your site, interacting as they normally would, but every bit of data they transmit is in plaintext.
In an SSL stripping attack, the attacker acts as a bridge. It’s making an HTTPS connection with the server and an HTTP connection with the client. That makes the connection appear secure — almost as if you were using a VPN, but the attacker is stealing data.
How Can You Prevent SSL Stripping?
There are two main tactics that can be used to avoid SSL stripping attacks.
- Only use the latest TLS protocol versions; and/or
- Add your website to the HSTS Preload List.
The Internet Engineering Task Force (IETF) and the creators of TLS have worked hard to shore up this problem. TLS 1.2 and, even more, TLS 1.3 have been designed to be resistant to these kinds of attacks. They encrypt more of the handshake — the portion where the connection is redirected.
Already, SSL 2.0 and 3.0 have been fully deprecated, and the major tech companies have announced plans to full deprecate TLS 1.0 and TLS 1.1 by January 2020. This is for good reason — TLS 1.2, and even more so TLS 1.3, is superior.
The other thing you can do is add your website to the HTTP Strict Transport Security (HSTS) preload list. You should already be using HSTS, which is an HTTP header that forces a client to make a secure connection to the website. If the client can’t reach an HTTPS version of the site, it just doesn’t connect.
But, the HSTS header needs to be downloaded first, so the very first time a client arrives at your website there’s a small attack vector for an attacker to SSL strip. The HSTS preload list closes this window. Once your site is included, any client will know to only make secure connections — even if they’ve never visited the site.
Updated versions of the list are pushed out alongside browser updates. All major browsers recognize the HSTS preload list.
Save Up to 82% on DV SSL Certificates
Protect a website in a few minutes with DV SSL or Domain Validated SSL Certificate.





