
Everything You Need to Know About SSL Inspection
Introduction: Need for SSL Inspection (a.k.a. HTTPS Interception)
With HTTP, all the data transferred between a website (server) and the user (browser) is in plain text, so if anyone manages to get access to the data in transit, they can read, interpret, and tamper with it. SSL certificates encrypt all the data in transit using a strong algorithm to keep the data secure.
The problem with SSL encryption is that it encrypts all data, so that even malicious data is encrypted and can reach its intended victim without getting noticed.
- An SSL certificate can’t discriminate between harmful and harmless data. That’s why its encryption facility is exploited by attackers to hide viruses, spyware, and other malware.
- With domain validated (DV) SSL, certificate authorities verify only domain ownership. So, it is very easy for attackers to enable SSL encryption on their own website and spread malware.
- Incidents of data leakage can also go unnoticed if the attackers are using an HTTPS channel while smuggling the data out. (For example, sneaking out digital documents with trade secrets from the organization’s network.)
To stop such exploitation, SSL inspection came into the wrestling ring.
How Does SSL Inspection Work?
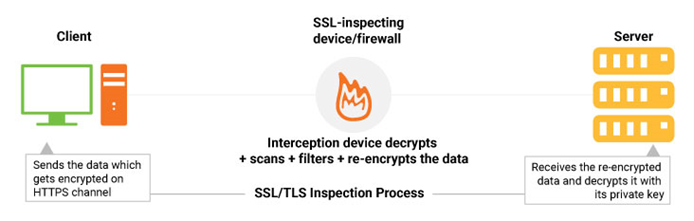
In traditional SSL mechanism, the data is encrypted and reaches to the intended receiver without being interrupted in the middle. In SSL inspection, there is an interception device sitting in the middle that scans and filters the data before it reaches the other party.
This interception device (also known as the middlebox) decrypts the incoming data, removes the suspicious data (if any), then once again encrypts the data and sends it to the intended user. It is like a man-in-the-middle attack but done with consent and noble intentions.
SSL inspection works for both inbound and outbound traffic. This means that it intercepts the traffic going both ways, sever to browser and browser to the server.

There are 2 popular products used for SSL inspection.
- Commercial hardware devices which perform traffic inspection on corporate networks. It enables administrators to monitor the data transferred to, from, and within the organizations.
- Anti-virus software and firewalls, which are usually run on users’ computers.
Disadvantages of HTTPS Interception
With SSL inspection, 2 separate SSL connections are made. One is between the server and the interception device, and another is between the browser and interception device. As you can imagine, the entire success of SSL inspection concept is depended upon the competence of the interception device.
To check the efficiency of the middlebox, a study was conducted by a team of cryptography industry experts, including Zakir Durumeric, Zane Ma, Drew Springall, Elie Bursztein, Nick Sullivan, Richard Barnes, Michael Bailey, J. Alex Halderman and Vern Paxson. According to their research report, 62% of middlebox connections were less secure, and an astounding 58% had severe vulnerabilities enabling later interception. They also investigated popular anti-virus and corporate proxies and found that nearly all of them (except Blue Coat by Symantec) reduced connection security and introduced vulnerabilities. They are using outdated cryptography to decrypt and re-encrypt the traffic, which significantly weakens the HTTPS and reduce the overall safety of the user’s data. (This study is a few years old, so some improvements in the technology have been implemented since then.)
Final thoughts,
SSL inspection is an excellent concept-theory wise. We don’t want to let malware or data leaks be encrypted and make its way right under our noses without getting noticed. As we mentioned before, the SSL inspection concept relies heavily on the efficiency of the middlebox. So if you enable SSL inspection, it’s critical that you select and configure a device that will maximize the security and efficiency of inspection.





