Everything you need to know about certificate transparency, certificate transparency logs, and why they matter
Certificate transparency (CT) is a comprehensive system that involves the logging, monitoring, and auditing of issued SSL/TLS certificates. These public logs contain cryptographically verifiable records of all the SSL/TLS certificates issued by publicly trusted certificate authorities (CAs). To meet requirements from Google, all CAs must log every certificate they issue in the certificate transparency logs. The main purpose of certificate transparency is to protect the website owners from mis-issuance and misuse of SSL certificates.
What Are the Features of Certificate Transparency Logs?
These are the key components of certificate transparency logs.
- CT logs serve as open, verifiable resources. CT logs are publicly verifiable, open-to-all databases for monitoring and auditing SSL certificates.
- CT logs provide access to certificate and issuer information. You can check any domain’s certificate issuer, location of the CA, issuance and expiry dates of an SSL certificate, subdomain coverage, history of all the previous certificates, and other important details in CT logs.
- CT logs are append-only databases. This means that whenever a CA logs a certificate’s details, it’s added to the database as a new record. The older records can’t be deleted, updated, or overwritten with newly changed data. This helps to prevent tampering issues.
- Records are cryptographically assured. Certificate transparency logs use Merkle tree hashes, which is a robust cryptographic technology that prevents tampering.
Why Are Certificate Transparency Logs Necessary?
The need for certificate transparency logs is increasingly important as cyber attackers seek to find new ways to exploit any loopholes that exist in current SSL/TLS certificate technology.
There are dozens of certificate authorities in the market. Any CA can issue an SSL certificate for any website on the internet. If a certificate authority’s private key is stolen, the attacker can issue the SSL certificate containing any website’s private keys and attach it to their own server’s private keys! They can send, receive, decrypt, and steal the data impersonating the original website. Neither the website visitor’s browser nor the website owner would even suspect that anything is wrong until it’s too late.
Publicly trusted CAs safely store their keys on a hardware security module (HSM), which is kept offline. However, there have been a few times when CAs’ keys were stolen and misused by cybercriminals.
Examples of Why Certificate Transparency Matters
We’ve put together a two examples of the most notable incidents involving stolen and misused SSL/TLS certificates:
The first example took place in August 2011. An Iranian attacker hacked Dutch certificate authority DigiNotar and issued a fraudulent certificate for google.com and all its subdomains. This attack primarily affected Iranian Gmail users. The good news for Google Chrome users? The browser was able to detect the phony certificate and shield users from it.
The second example we’ll share occurred in March 2011. An Iranian attacker hacked the certificate authority (then called Comodo CA) via instantssl.com and issued himself certificates for some notable websites, including Gmail, Hotmail, and Yahoo Mail.
As you can see, the faulty issuance of an SSL certificate can have dire consequences. CT logs can’t prevent the mis-issuance the SSL certificates. But if any suspicious certificate has been issued, a CT log’s monitors and auditors can quickly detect and revoke the certificate to minimize damage at the earliest stage.
Who Runs the Certificate Transparency Logs?
Currently, Google is running multiple certificate transparency logs through its Certificate Transparency Project. The goal of this initiative is to “safeguard the certificate issuance process by providing an open framework for monitoring and auditing HTTPS certificates.” Their website indicates that more than 8.2 billion entries have been made to the CT logs that they monitor!
The purpose of monitoring and auditing is to protect the integrity of the certificate transparency logs. In general, certificate monitors fall under the responsibilities of the CAs, whereas auditors are operated by the browsers. They continuously keep an eye on unauthorized certificates, unusual certificate extensions, or certificates with unusual powers.
How Do CT Logs Work?
Let’s dive into how certificate transparency logs work at a basic level. Anyone can submit a certificate to the log. However, if you’re a website owner or website visitor, it’s not your job to add your certificate details to CT logs. This task is typically left to the CAs and server operators.
Your CA should submit an SSL certificate to the CT logs and embed a signed certificate timestamp (SCT) in the certificate before sending it to you. SCT is the assurance that the log servers will add the certificate to the CT logs within a specific time period. (In a way, an SCT is like a learner’s permit — a temporary document you can use until you get the real driver’s license). When the browsers try to verify the SSL certificate during the TLS handshake process, the SCT is also presented with the certificate, so that the browsers don’t block the certificate or show an error message. The SCT is delivered through an X.509v3 extension, TLS extension or OCSP stapling.
Check out the diagram below to get a clear idea on how SCT delivering process works and compare it with the current TLS/SSL system (i.e. when there are no SCT initiated)
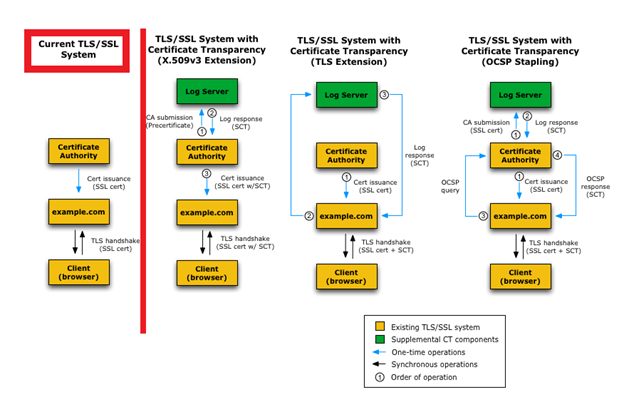
Diagram courtesy of certificate-transparency.org
If you want to check any website’s CT logs, simply go to Google’s Transparency Report page and write down the domain name in the “Search certificates by hostname” field.
What If My Certificate Authority Hasn’t Logged My Certificate’s Information in CT Logs?
If the CA accidentally or intentionally doesn’t record the information about your domain’s SSL certificate in CT logs, no browsers would trust your website’s SSL certificate. As a result, all the browsers will show the dreaded “Your Connection Is Not Private” page with the “ERR_CERTIFICATE_TRANSPARENCY_REQUIRED” error message displayed on it (much like how the screenshot below looks):
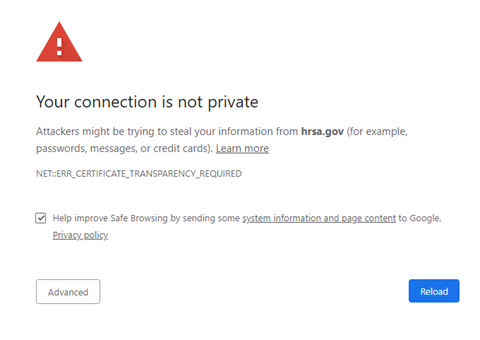

To bypass the error page, users must manually click on the Accept Risk tab every time they visit your website, which can drastically affect your website traffic and business in a negative way. If you see “ERR_CERTIFICATE_TRANSPARENCY_REQUIRED” error on your website, immediately contact your CA and ask them to log your certificate’s details in CT logs.
Reputable CAs are not negligent and are very careful to ensure that every certificate is carefully logged in one of the certificate transparency logs. DigiCert is considered one of the top CAs in the industry. We strongly recommend you using SSL/TLS certificates from DigiCert or one of its subsidiaries (such as RapidSSL, Symantec, GeoTrust, and Thawte), which start as low as $12.42 per year, to avoid such risks of omittance.
Save Up to 82% on SSL Certificates from RapidSSLonline!
Protect your website with an SSL Certificate from brands like RapidSSL, Symantec, GeoTrust, and Thawte.





