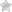What is the difference between private key vs public key encryption? It may not be what you think
“SSL Public Keys and SSL Private Keys are like ebony and ivory, living together in perfect harmony. Side-by-side on the piano keyboard, oh Lord, why don’t we.” — Paul McCartney and Stevie Wonder, when they addressed the difference between public and private keys in cryptography.
The above quote about public keys and private keys is fake, obviously. But we know if got your attention. Now, without further ado, we’ll explain the difference between public key and private key encryption.
Public Key vs Private Key Cryptography
In SSL, and in public key infrastructure (PKI) in general, keys are used to perform a range of cryptographic functions. When a client arrives at a website, the two use their public and private keys during a process called the SSL handshake. That handshake creates a third key, what’s known as a session key, to communicate during the connection.
A session key is symmetric, meaning it’s capable of both encrypting and decrypting. They tend to be smaller, but perform better and still offer ample security. When you communicate online, you’re using one of those symmetric session keys. You don’t use the public and private keys to communicate. Anyone that tells you that is a Charlatan and you should smite them where they stand.
The Roles of Public Keys vs Private Keys in Encryption
So, what do the public and private key do? Well, probably not what you think. Public/private key pairs are asymmetric — the public key can encrypt, and the private key can decrypt. Historically, when the RSA cryptosystem is in use, the public/private key pair handles the transmission of the session key. After all, how else would you exchange and encryption key securely?
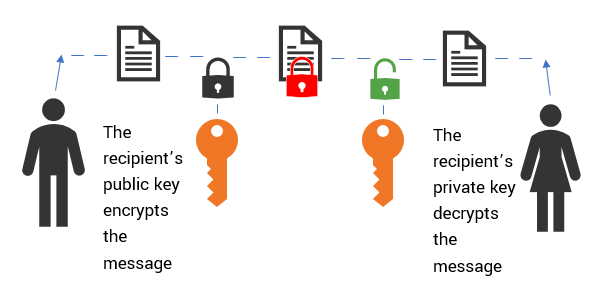
With RSA key exchange, the pre-master secret that will be used to derive the session key is encrypted with the public key, sent to the server and decrypted with the private key.
How These Roles Have Changed in TLS 1.3
In TLS 1.3, RSA key exchange was banned. So… this means there’s no longer asymmetric encryption in the handshake.
Let’s take a moment because that bears repeating: THERE IS NO LONGER ASYMMETRIC ENCRYPTION OCCURRING DURING THE HANDSHAKE SINCE TLS 1.3 KICKED IN.
So, what do the public/private key pair do now? Digital signature authentication. Owing to the nature of the two keys, the public key can be used to verify signatures left by the private key. When a client is presented with a certificate, it uses the corresponding public key to trace the signatures back up the certificate chain and to its root store.
This is now the only use case for the public/private key pair as of TLS 1.3.
Save Up to 82% on DV SSL Certificates
Protect a website in a few minutes with a Domain Validated SSL Certificate (DV SSL).