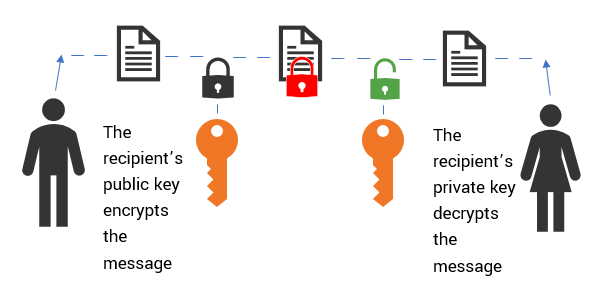
A primer on what each of these encryption terms entails and their impact on
website security
TLS vs SSL vs HTTPS. So many acronyms, so little time. All
of these terms relate to encryption and website security — however, many people
who don’t spend their days entrenched in cyber security may not be intimately
familiar with them.
HTTPS, an encrypted and secure networking protocol, is what
we get when we use SSL/TLS
to secure websites. You know how there’s a padlock security indicator in your browser’s
address bar? Yeah, it’s because of that (and other things we aren’t going to
get into here).
One of the most common questions we get regarding the topic
of TLS vs SSL is “what the difference is between SSL and TLS?” The confusion
makes sense, in a way. After all, SSL and TLS aren’t exactly the same
thing, but they serve the same function.
So, how do we split the difference?
And the answer to that is incredibly technical — far more
technical than most people care to go. So, we’re going to summarize it for you
so you can rent it space in your brain at the expense of some other far more
relevant piece of information. Say goodbye to the Pythagorean Theorem — we’re
about to talk about SSL and TLS.
SSL — The OG
SSL,
or secure sockets layer, was the original lynch pin of public key
infrastructure (PKI). Initially, the internet was not designed for commercial
use. It was basically just a network for the military and academia in its
earliest iterations. As commerce and other vital services crept online, the
need for data security arose. Unfortunately, HTTP or the Hypertext Transport
Protocol, was never designed for security, so a mechanism needed to be invented
to secure it.
Thus, SSL and HTTPS were born. The first couple of SSL
versions were failures and never really got off the ground. SSL 3.0 was
eventually released but was quickly found to be vulnerable to several exploits,
too. That was 1996.
Enter TLS
TLS, or transport layer security, was created in 1999 as
kind of a spiritual successor to SSL 3.0. It’s based on SSL, but there’s one
really important, key difference — this isn’t the House of Saxe-Coburg and
Gotha renaming itself the Windsors as a branding move — it’s an actual
functional difference.
Knowing the Difference: SSL vs TLS
What’s the difference between SSL and TLS? SSL makes it
connections by port. In computer networking, a port refers to a memory
address that’s used to help organize traffic during a connection. This occurs
at the transport layer of the connection; individual services have dedicated
ports. 443 is the port for HTTPS. 80 is the port for HTTP. 21 is for FTP and so
on. There are 65,535 ports total, and only a set few are dedicated to a
particular service or function.
Since SSL makes its connections via port, it starts with
port 443 for an HTTPS connection. This is called an explicit connection,
and the port expects a negotiation before the session begins.
TLS, on the other hand, connects via protocol. This
is an implicit connection. It begins with a client hello via an insecure
channel to the server. Once the handshake commences, the connection switches to
the correct port (443).
A lot of the other parts are basically the same. Both
protocols authenticate and facilitate encryption. They both negotiate with
handshakes. It’s the way that initial connection is made that differentiates
the two. The security they both provide is exactly the same.
Problems with TLS
TLS is, by no means, faultless. While SSL was riddled with
vulnerabilities, the early iterations of TLS also had their fair share of
hiccups, too. POODLE,
which stands for Padding Oracle On Downgraded Legacy Encryption, is a padding
attack that can be used against block ciphers. This sick little puppy was
basically the final nail in SSL 3.0’s coffin. They thought they fixed it with
TLS. Needless to say, they were mistaken.
As it turns out, POODLE didn’t die. We still seeing variants
of POODLE to this day. There are also exploits like downgrade and stripping attacks
that take advantage of the backward compatibility that was included in TLS in
the name of interoperability.
TLS 1.0 and TLS 1.1 are now considered insecure, with the
major tech companies planning a mass deprecation of both by January 2020. TLS
1.2 is the current standard while TLS 1.3 was just finalized in Summer 2018.
TLS 1.3 Looks Toward the Future
TLS
1.3 will change SSL/TLS forever simply because it’s not backward compatible
with any of the previous protocol versions. Currently, you have to support TLS
1.2 and 1.3 side by side, as users can’t roll back to 1.2 from 1.3.
In addition to eliminating backward compatibility, which
should kill off older protocol versions, TLS 1.3 made several significant
improvements over previous iterations:
- It reduced the handshake, which adds latency to
connections, to a single roundtrip and added 0-RTT resumption.
- It eliminated older ciphers that have been found
vulnerable, like RC4 and RSA.
- It reduced the number of negotiations made
during the handshake to just two.
What’s Better: TLS vs SSL
Given their similarities, and the known vulnerabilities
facing SSL, this really should only be asked rhetorically. You did mean
this rhetorically, right?
If you’re still supporting SSL, you’re only inviting
trouble. Even supporting earlier versions of TLS is ill-advised. You should be
using TLS 1.2 and TLS 1.3 by now.
SSL may be TLS’ predecessor, but it’s seriously outmoded now. Even if it’s still what we use colloquially to refer to TLS.