Understand SSL Industry Big Changes SHA-2 Algorithm
It seems SHA-2 algorithm is efficiently revolutionizing the Internet Security scene. All the big names from the industry are now rooting for SHA-2 and deprecating their support towards SHA-1, the predecessor of SHA-2. So, let’s have a look at why and how this SHA-2 revolution is taking place.
The SHA Digital Signature Algorithm Discovery
Secure Hash Algorithm (SHA) was published by the National Institute of Standards and Technology (NIST). Basically, it is a set of cryptographic hash functions developed with an intention to maintain and enhance security and integrity on the Internet. The NIST published SHA as a US Federal Information Processing Standard (FIPS). The following are the current members of the SHA family:
SHA-0: The original version which was published in 1993. It was of 160-bit hash function and was soon withdrawn after its publication due to major flaws, which were not disclosed.
SHA-1: It resembles the earlier MD5 algorithm. It is a 160-bit hash function, which was designed by National Security Agency (NSA) to become a part of the Digital Signature Algorithm. However, after finding a few discrepancies in its performance, and post 2010, many experts believed it to be unfit for any cryptographic usage.
SHA-2 – SHA-2 was designed by the NSA as well. This algorithm is gradually replacing its previous version, SHA-1. SHA-2 consists of two hash functions, SHA-256 & SHA-512. Both of these hash functions are mostly similar, but have different block sizes.
Research on SHA-2 New Algorithm
Developed by the National Institute of Standards and Technology (NIST) & National Security Agency (NSA), SHA-2 algorithm offers a high level of security as compared to its predecessor, SHA-1. This set of algorithms is patented in US 6829355 and is released under royalty-free license by the United States. Currently, it consists of the following algorithms:
- SHA-256 and SHA-512: These hash functions are computed with 32-bit and 64-bit words respectively. Despite using different shift amounts and additive constants, structure-wise, both of them are almost identical. The only difference is the number of rounds in their structures.
- SHA-224 and SHA-384 – These hash functions are commonly referred to as the ‘truncated’ versions of SHA-256 & SHA-384. The initial values of both of them are different.
- SHA-512/224 & SHA-512/256 – Apparent by the way these hash functions are named, both of them are the truncated versions of SHA-512.
Why the Transition to SHA-2?
SHA-1 is a message digest algorithm, which was published in 1995 as a part of Secure Hash Standard (by NIST). Ever since it was introduced, SHA-1 went on to become the most popular choice of any Certificate Authority (CA).
Now, as per the basic rule, a hashing algorithm is considered to be safe for use only when it is capable to produce unique output for any given input. Also, the output should not be reversed as the function must work in one way. And ever since 2005, researchers and experts have found SHA-1 to be the victim of collision attacks. In such attacks, multiple inputs can produce the same output, which means that SHA-1 was no longer capable of fulfilling the security criteria for forming a cryptographically safe message digest.
Here is a time-line of the attacks carried out on SHA-1 SSL certificates. Also, researchers found striking similarities between MD5 Attacks and the attack carried out on SHA-1 (as noticed in the Cryptanalysis of MD5 and SHA-1 by Marc Stevens):
- 1995: SHA-1 published
- 2005: SHA-1 collision attack published in 2^69 calls
- 2005: NIST recommendation for movement away from SHA-1
- 2012: Identical-prefix collision 2^61 calls presented
- 2012: Chosen-prefix collision 2^77.1 calls presented
The deprecation of the SHA-1 algorithm was actively initiated in 2011. Certificate Authorities (CAs) and the industry group of leading web browsers at CA/Browser Forum teamed up to establish some basic security requirements for SSL certificates. They also published their ‘baseline requirements for SSL’, which advised all CAs to move from SHA-1 to SHA-2.
Till date, there has been no occurrence of a successful complete collision with SHA-1, but it concerns are arising due to the evolution of computers’ calculation capacities. However, SHA-2 users can breathe a sigh of relief as this algorithm is completely collision-free.
We are all aware how sophisticated cyber-attacks have become these days. So, it is quite logical for an algorithm developed almost two decades ago, to become weaker and act vulnerable toward the advanced technologies used by attackers. And, as a result, it makes perfect sense for users to move on to a stronger hash algorithm with the computational power that is strong enough to resist attacks and for maintaining security on the Internet.
Web Servers Compatible with SHA-2 Algorithm
Here is a list of servers that are found to be compatible with the SHA-2 algorithm:
- Apache server (tested with Apache 2.0.63 and Open SSL 0.9.7m. It requires OpenSSL 0.9.80+ for complete implementation)
- Windows Server 2008+
- Windows Vista
- Windows Server 2003 with patch 938397
- Windows Server 2003 or XP client with patch 968730
- Oracle WebLogic from the version 10.3.1, see bug8422
Web Browsers Compatible with SHA-2
All the browsers on this list are compatible with the SHA-2 algorithm:
- Internet Explorer under Seven and higher
- Internet Explorer 7+ under Vista
- Internet Explorer 7+ under Windows XP SP3
- Firefox 1.5+
- Netscape 7.1+
- Mozilla 1.4+
- Safari from Mac OS X 10.5
- Opera 9.0+
- Mozilla products based on NSS 3.8+ (since April 2003)
- Products based on OpenSSL 0.9.8o+
- Java 1.4.2+ based products
- Chrome under Windows Vista and higher
- Chrome under Mac from Mac OS X 10.5
- Chrome under Linux
SHA-2 Cryptography Applications
Although SHA 2 is not yet as widely used as its predecessor, SHA 1, here is a list of a few of its applications:
- This algorithm is widely implemented in popular security applications and protocols like SSL, TLS, IPSec, S/MIME, SSH, PGP etc.
- There are many Crypto currencies that rely on SHA-2 as a part of their proof-of-work scheme.
- Just like SHA-1, SHA-2 is also needed by law, to be used in many US government applications.
- SHA-2 rightfully performs the most basic SHA function of effectively verifying the procedure of message authentication along with password verification as well.
- Authenticating Debian, GNU/ Linux & DKIM Message signing standard are performed using SHA-2.
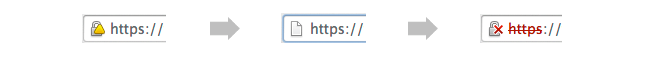
- Chrome 39: Set to be released in November 2014, any SHA-1 SSL certificates expiring on or after January 1 2017 will trigger ‘secure, but with minor errors’ on the browsers. In this, a little yellow symbol would be displayed on the padlock as shown in the image below.
- Chrome 40 – This version is expected to be released after the holiday season. Here, the web-pages that are secured by SHA-1 certificates, which are expiring between June 1 2016 to December 31 2016 will trigger the yellow symbol warning of ‘secure with minor errors’ and the certificates expiring on or after January 1 2017 shall be treated as ‘neutral, lacking security’. In this, a blank page icon replaces the padlock. Please see the image given below.
- Chrome 41 – Expected to release in the second quarter of 2015, using SHA-1 SSL certificates on this browser with expiration dates between January 1 2016 and December 31 2016 will result in the ‘Secure with minor errors’ warning. However, the certificates expiring on or after January 1 2017 will trigger the ‘affirmatively insecure’ warning, in which the padlock gets a striking red cross on the URL as shown in the last image above.
Steps Taken Against the Usage of SHA-1 Certificates
As the world of cryptography was introduced with the downsides of using the SHA-1 SSL certificates and simultaneously the benefits of choosing SHA-2 certificates instead, there were several Internet giants like Microsoft, Google, etc. that raised their voice against the usage of the vulnerable SHA-1 SSL certificates by coming up with specific deprecation policies for their users. Here is what the latest SHA-1 deprecation scenario looks like:
Microsoft Deprecation Policies
Last year, in November 2013, Microsoft© announced new policies for all the Certificate Authorities (CAs) based on the concerns that SHA-1 is no longer secure enough. As per these SHA-2 favoring policies, the company disapproves the use of SHA-1 algorithms in SSL and code signing certificates.
The following are the deadlines included in these policies, looking at which the users can interpret the seriousness of the threats by using SHA-1 certificates:
| Date | |
|---|---|
| January 1, 2016 | All the CAs must stop issuing new SHA-1 SSL and Code Signing certificates |
| January 1, 2016 | For Code signing certificates, Windows will no longer accept SHA-1 code signing certificates without any stamps. |
| January 1, 2017 | Windows shall not accept any SHA-1 end-entity certificates |
Google Stops Supporting SHA-1
Recently, it was the search engine giant, Google© to announce its own deprecation policies against the usage of SHA-1 SSL certificates. These policies are projected to be applied in the company’s upcoming versions of Chromium web browser. The deprecation pattern has been designed by Google as follows:
How to Migrate for New SHA-2 Algorithm?
It would be really advisable to first check your website, whether it’s using SHA-1 or not. Please click here to check if your site is relying on SHA-1 SSL certificate.
Based on your findings, you can proceed to the migration process by contacting the CA of your SSL certificate, who would help you migrate from SHA-1 to SHA-2. Most of the authorities offer easy-to-follow procedures to streamline migration process. Here are few simple steps for all the existing and the new customers of RapidSSLonline, who intend to re-issue or issue an SSL certificate with SHA-2 algorithm:
Existing Customer: The existing customers of RapidSSLonline, can re-issue their SSL certificates with SHA-2 by following this simple method:
Step 1 – Go to the ‘Order Listing’ page and click on the “view”’ option to see order details page. On the order detail page, click on the re-issue button which is located on the bottom side on the same page.
Step 2 – After that, you shall receive an e-mail from RapidSSLonline, which contains a centralapi link.
Step 3 – On clicking the centralapi link, you will be re-directed to the panel of ‘Certificate Re-issue’.
Step 4 – Please enter your SSL certificate’s CSR with SHA-2 and then carefully select SHA-2 from the drop down menu given for ‘Algorithm.
Step 5 – After performing the above step, you will soon have your SSL certificate re-issued to you via e-mail, which you can download and install on your website by following the routine procedures.
New Customer: All the new customers at RapidSSLonline can issue a brand new SHA-2 SSL certificate by performing the steps mentioned below.
Step 1 – As a fundamental step, the customer should first generate a new CSR by choosing the SHA-2 algorithm.
Step 2 – Now you can proceed to order the certificate by clicking on the ‘Generate Certificate’ button.
Step 3 – Next, you would be directed to the panel of ‘Certificate Issuance’ process panel. Here, you need to enter the CSR you generated in the first step.
NOTE: It is very important here to make sure you select SHA-2 algorithm while ordering.
Step 4– Your new SSL certificate shall be soon e-mailed to you by the authorities.






 (2 votes, average: 4.00 out of 5)
(2 votes, average: 4.00 out of 5)