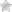Understand Vulnerabilities and Their Causes to Secure Website
The hits just keep on coming! We have yet again bumped into another software bug that threatens our web security. It has been hardly 5 months since the discovery of the ‘Heartbleed’ bug and now another nasty surprise has been uncovered, called ‘Shellshock’.
What is the Shellshock Bug?
The Shellshock bug is the latest vulnerability that is likely to affect several versions of Linux and Unix operating systems. This was discovered by Linux expert Stéphane Chazelas on September 2014 in the UK. Linux-based web routers having web interface (using Common Gateway Interface) are also found to be vulnerable to Shellshock.
Alternately known as the Bash Bug, Shellshock is likely to be more severe compared to the Heartbleed Bug. As per the security experts, attackers can easily exploit the bug in the Bash and take complete control of the system being targeted. The United States Computer Emergency Readiness Team (US-CERT) of the Department of Homeland Security has issued an alert about this vulnerability affecting the Unix-based operating systems such as Linux along with Apple’s Mac OSX.
How Does Shellshock Bug Attacks?
A remote attacker can easily exploit Bash under definite circumstances. The attacker just needs to manage to force an application for sending a malicious environment variable to the bash.
Attackers are most likely to choose the route via web servers using the Common Gateway Interface (CGI), which is the most popular system used for creating dynamic web content. But, attackers tend to use it or exploit it to send malicious environment variable to the target system. As the Bash is used by the server for interpreting the variable, automatically it will also run the malicious command that was inserted.
The following diagram depicts how a malicious command can be injected at the end of a legitimate environment variable, which is later run by Bash.
Serious consequences follow, once an attacker is successfully able to exploit this vulnerability on a server. It may allow attackers to download harmful malware on the targeted computers or dump password files. Similarly, attackers can also compromise and attack other devices in the network after entering the firewall of the victim’s computer.
Why Shellshock is projected to be more harmful than Heartbleed
The severity of the aftermath caused by this bug can be understood only after highlighting the importance of the element it affects, the Bash.
To be precise, the vulnerability caused by Shellshock affects the UNIX Bash Shell. Bash, also known as Shell, is the common component of several versions of Linux and UNIX. The function of Bash is to perform as the command language interpreter, which means it allows the users to type the command in a simple text-based window that the operating system can run.
Bash is also used to run the commands, which are passed on by the applications. This happens to be the very feature that is exploited by the Shellshock bug. These environment variables are very dynamic, named values that directly affect how the processes are run on a computer. So, the weakness being exploited here is that the attacker can easily introduce a malicious code on to the environment variable, which will be run after the variable is received.
On the Common Vulnerability Scoring System (CVSS), Shellshock has received a straight 10/10, which makes it one of the biggest and most notorious bugs we have seen in the history of the Internet. And looking at the immense presence of the Bash shell, a large number of internet devices shall end up being vulnerable to Shellshock such as routers, Linux systems, Macs, web servers etc.
Apparently, Bash is the most widely used software in web servers at various organizations. Shellshock enables cyber criminals to attack a web server with the convenience of remote access to compromise the host. Once the victim organization is compromised, an attacker can completely take over the system, unlike Heartbleed – a bug in OpenSSL, where attackers could just spy on computers and not take the control of the system completely.
Procedure to Check your Computer’s Vulnerability
Rather than fretting about when and how your computer is going to get affected by Shellshock, it is advisable to find out for real if or not your computer is vulnerable to this bug. Here is a little procedure for that:
- Open the terminal on your computer and run the following command:
env x='() { :;}; echo vulnerable' bash -c "echo this is a test" - You will see the following, if your system is vulnerable to the Bash:
vulnerable this is a test
- However, if your system is well-patched and protected, you will see the following message being flashed:
$ env x='() { :;}; echo vulnerable' bash -c "echo this is a test" bash: warning: x: ignoring function definition attempt bash: error importing function definition for `x' this is a test
Tips to Reduce the Risks of a Shellshock bug
Users can follow the tips mentioned here to reduce the risks of falling prey to this bug:
Online Businesses: All users of Linux/Unix-based systems are recommended to implement the patches immediately. The following are a few patches that have been released by their respective vendors:
- Debian— https://www.debian.org/security/2014/dsa-3032
- Red Hat— https://access.redhat.com/articles/1200223
- CentOS— https://centosnow.blogspot.com/2014/09/critical-bash-updates-for-centos-5.html
- Novell/SUSE— https://www.suse.com/security/cve/CVE-2014-6271.html
Please note, Red Hat has updated its advisory for Shellshock after noting that its initial patch is incomplete.
Consumers: For consumers, it is advisable to apply patches to the routers and any other web-enabled devices, as and when the vendors provide them.
However, if the patch is not yet released for a particular Linux/ Unix, it is recommended to shift to an alternate shell till a proper patch is provided by the vendor.