Don’t ever let someone else touch your private key without your consent.
Today we’re going to discuss Public Keys, Private Keys and Encryption. Unfortunately, a lot of the literature on this topic around the internet is needlessly complicated. And when I say needlessly complicated I mean some developer or programmer wrote it using nomenclature that only another developer or programmer would know.
It’s kind of like how academics and modern philosophers write dense, difficult to understand texts as a way of both showing off their intelligence and to try and one-up their contemporaries. And in these philosophical personal pissing matches, the layman is just kind of caught in the middle saying, “whaaaat?” There may be some good information in those texts, but to most of us—we’re just getting rained on.
I am not like that. I am conscientious of my readers. Call me Conscientious Carl. And I’m going to explain these concepts to you in basic English, using terms you can understand. I don’t get off on using big words or fancy tech-speak like some people do. Though, now that I think about it, that would make for a good Silicon Valley phone sex line. “Yeah baby, tell me how you’re going to side-jack me by using your packet sniffer on my cookies.” [Editor’s Note: Carl…]
Anyway, let’s talk about Public and Private keys.
Batman, A Horse’s Rear and Two Types of Encryption
There are two kinds of encryption, symmetric and asymmetric. Do I need to explain symmetry? Would that be patronizing? [Editor’s Note: Only a little] Ok, I’ll just use an image. This is an example of symmetry:
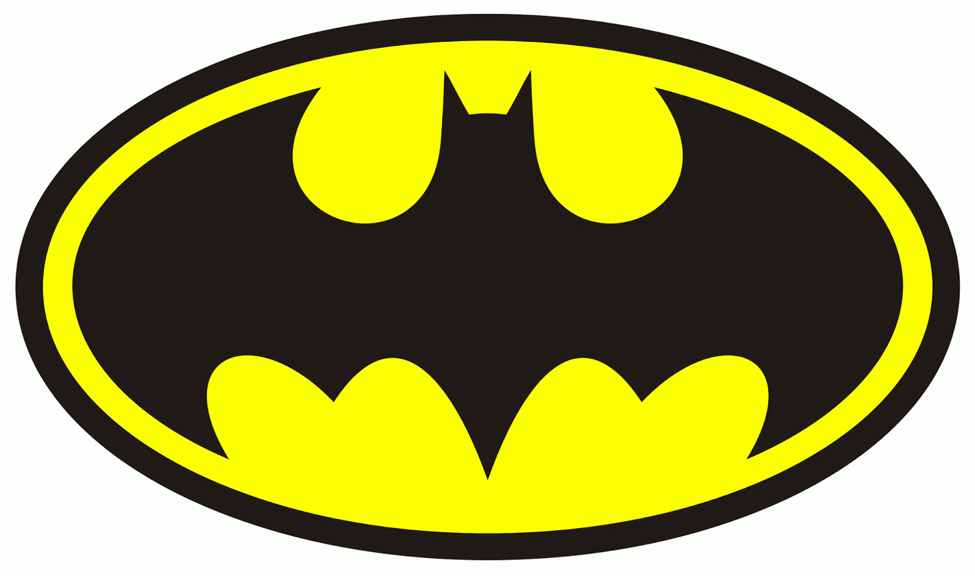
See how you could draw a line right down the middle and it would be the exact same (though mirrored) on both sides? That’s because the Batman logo is both bad ass and completely symmetric. And thank you for humoring me, I have been looking for an excuse to use this image since I took the blog over.
This is an example of asymmetry:
Notice how if you drew a line down the middle of this picture the two sides are not mirror images of one another? They’re not the same. You could say this is ass-ymmetric. This picture is actually doubly relevant because if you legitimately needed me to explain symmetry to you then you are indeed a horse’s [Editor’s Note: Yeah… I’m not going to let you finish this sentence, Carl]
Ok, we’ve gone too far into the weeds, something I would not advise doing around this horse lest you’re wearing boots. And even then… [Editor’s Note: CARL!]
So how does this apply to encryption? I’m glad you asked. As we already established, there are two kinds of encryption. The first type, symmetric encryption, occurs once a secure connection has been established. It uses symmetric session keys that can both encrypt and decrypt communication. That’s another discussion for another time, though.
Then there is asymmetric encryption, that’s what we’re going to be talking about today. This occurs during the SSL handshake and helps your web browser to authenticate the website’s SSL certificate in order to establish a secure connection.
Asymmetric Encryption is a lot Like My Marriage
Asymmetric encryption occurs during the SSL handshake and uses a Public Key and a Private Key. Here’s how it works:
- Your browser reaches a website with an SSL certificate. After both say “Hello” – because browsers and servers are nothing if not polite – the browser receives a copy of both the certificate and the accompanying public key.
- The browser then uses the public key to encrypt a small bit of throw-away data and send it back to the server. The server uses the corresponding private key to decrypt what was sent and send it back as plain-text (meaning in its unencrypted form). If the server returns the same data that was originally encrypted, it verifies the key pair to the browser.
Now, when I say the key pair, I mean that the public and private key match. This is just a portion of the handshake (again, another discussion for another day), but an integral one nonetheless.
Here’s another way to think about it. The public key, like my wife, does most of the talking. It says something, which it has encrypted in a way that it thinks will only make sense to me. It’s then my job to decrypt whatever it is she just said and repeat it back to her to make sure I got it right. If I didn’t, I get in trouble.
Public and Private keys are the same way, just far less passive aggressive. Public keys also fix a better casserole, but I digress.
Let’s Wrap This Up
So there you have it. Public keys and Private keys are an example of asymmetric encryption. One key sends data, the other decrypts it. This is done to verify that the keys match during the SSL handshake.
The actual communication that occurs after the handshake is done with symmetric keys that can both encrypt and decrypt. It’s really very simple, provided you have someone to explain it to you in a simple, if slightly chauvinistic [Editor’s Note: Slightly?] way.
Stay Cautious, My Friends.







 (6 votes, average: 3.67 out of 5, rated)
(6 votes, average: 3.67 out of 5, rated)