Stay Secure for Android Base Smart Phone Applications with SSL Certificates
Shocking results awaited us when a survey was carried out recently by a digital security firm, FireEye, on the Android applications. As per the findings, almost 68% of the top 1000 applications in Google Play store are vulnerable to at least one major SSL security flaw.
These flaws can range from applications not checking SSL certificates or using obsolete host name verifiers or simply ignoring SSL errors in the Webkit engine that generally signals the security problems. Any single flaw mentioned here is capable enough to enable / permit hackers to carry out Man-in-The-Middle attacks, where the attackers can easily compromise a user’s private data by a malicious party without the developers or the users knowing it.
Android Under Attack
Android is skillfully designed to be a modern, open-platform for the users. The wealth of Apps available on the Google Play Store is one of the main reason behind the popularity of the Android platform. Android applications use their devices advanced hardware and software along with local and served data, which is exposed through the platform to bring innovation and value to the customers. Now, to sustain this value, the platform needs to offer an application environment, which ensures the security of users’ identity, data, applications, device and the network they are using.
However, with each passing day, the number of malicious mobile applications are increasing. These infected/ affected applications can easily access the sensitive information stored on a mobile device. Such compromised information can be used by the hackers to carry out more such attacks with the help of different threat vectors.
Applications, as we know, interact with remote servers for their functionality. They normally communicate using either the:
- HTTP Protocol: This makes the data-interception for others very easy
- HTTPS Protocol: Due to the security measures involved in this, the data-interception becomes difficult. These security properties in HTTPS stem from the SSL & TLS certificates.
The Android platform provides libraries and methods to communicate with the servers by using secure network protocols such as HTTPS, and forming the underpinnings of PKI (Public-Key Infrastructure) implementations. The protocol of SSL/TLS is designed to enhance the security, but incorrect use of the libraries of Android platform can expose applications to MiTM attacks. In such attacks, the attackers can interpret the traffic flowing from the application to the server or vice versa and may:
- be eavesdropping and accessing the data sent by the server or the application
- modify the intercepted data or replace it with malicious code or data and re-introduce it in the application and redirect the traffic to an entirely new destination, which is controlled by the attacker.
Vulnerable Play Store
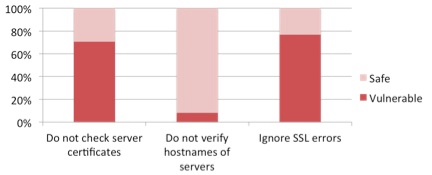
On July 17 2014, a team of experts at FireEye, reviewed as many as 1000 free applications from Google Play, which are very popular and are downloaded the most. Out of these 1000 applications, 68% (~ 614 applications) had at least one out of three SSL vulnerabilities. The number of vulnerable applications found in each category is presented in the image below:
How to Secure An Android App?
Following main steps are involved in securing the connection from a trusted Certificate Authorities CA:
Step 1 – Obtain all the required certificates (including root and any intermediate Certificate Authorities)
Step 2 – Next, create a keystore with a keytool and the BouncyCastle provider and import the certificates.
Step 3 – Load the keystore into the Android applications and establish secure connections
NOTE: Experts recommend not to use the standard java.net.ssl.HttpsURLConnection for securing the connection. Instead, it is advisable to use the Apache HttpClient (currently at Version 4) library, as it is already a built-in feature in Android. It is built on top of the java connection libraries and is considered faster, well modularized, and easy to understand.
Step 1 – Obtain the Certificates
In this step, you have to obtain all the certificates that are involved in building a chain from the endpoint certificate until Root CA, including Intermediate certificates as well, if any. However, it is not necessary to obtain the endpoint certificate.
If provided, users can obtain those certificates from the chain included in the endpoint certificate. Alternatively, they can obtain the certificates from the official site of the issuer.
Please make sure to save all the obtained certificates in the Base64 encoded X.509 format. The content should be looking like this:
1-----BEGIN CERTIFICATE----- 2MIIGqTC.....(continues) 3-----END CERTIFICATE-----
Step 2 – Keystore Creation
To start with, download the BouncyCastle package and carefully store it at a known location. At this stage, please make sure you can invoke the keytool command, which is usually located under the bin folder of the JRE installation.
Next, import the obtained certificates (not the endpoint certificate) into a BouncyCastle formatted keystore. It is advisable to import the certificates starting with the lowermost Intermediate certificate and then gradually moving all the way up to the Root CA certificate.
After giving the following command, a new keystore with password ‘mysecret’ will be created and the Intermediate CA certificate will be imported. Please execute this command for all the certificates:
keytool -importcert -v -trustcacerts -file "path_to_cert/interm_ca.cer" -alias IntermediateCA -keystore "res/raw/myKeystore.bks" -provider org.bouncycastle.jce.provider.BouncyCastleProvider -providerpath "path_to_bouncycastle/bcprov-jdk16-145.jar" -storetype BKS -storepass mysecret
Now verify if the certificates are imported in a correct manner into the keystore:
keytool -list -keystore "res/raw/myKeystore.bks" -provider org.bouncycastle.jce.provider.BouncyCastleProvider -providerpath "path_to_bouncycastle/bcprov-jdk16-145.jar" -storetype BKS -storepass mysecret
Should output the whole chain
RootCA, 22.10.2010, trustedCertEntry, Thumbprint (MD5): 24:77:D9:A8:91:D1:3B:FA:88:2D:C2:FF:F8:CD:33:93 IntermediateCA, 22.10.2010, trustedCertEntry, Thumbprint (MD5): 98:0F:C3:F8:39:F7:D8:05:07:02:0D:E3:14:5B:29:43
Now, the keystore can be copied as a raw resource in the android application under res/raw/
Step 3 – Use the Keystore in the Application
First, the user needs to create a custom Apache HttpClient that uses this keystore for HTTPS connections:
public class MyHttpClient extends DefaultHttpClient {
final Context context;
public MyHttpClient(Context context) {
this.context = context;
}
@Override
protected ClientConnectionManager createClientConnectionManager() {
SchemeRegistry registry = new SchemeRegistry();
registry.register(new Scheme("http", PlainSocketFactory.getSocketFactory(), 80));
// Register for port 443 our SSLSocketFactory with our keystore
// to the ConnectionManager
registry.register(new Scheme("https", newSslSocketFactory(), 443));
return new SingleClientConnManager(getParams(), registry);
}
private SSLSocketFactory newSslSocketFactory() {
try {
// Get an instance of the Bouncy Castle KeyStore format
KeyStore trusted = KeyStore.getInstance("BKS");
// Get the raw resource, which contains the keystore with
// your trusted certificates (root and any intermediate certs)
InputStream in = context.getResources().openRawResource(R.raw.mykeystore);
try {
// Initialize the keystore with the provided trusted certificates
// Also provide the password of the keystore
trusted.load(in, "mysecret".toCharArray());
} finally {
in.close();
}
// Pass the keystore to the SSLSocketFactory. The factory is responsible
// for the verification of the server certificate.
SSLSocketFactory sf = new SSLSocketFactory(trusted);
// Hostname verification from certificate
// http://hc.apache.org/httpcomponents-client-ga/tutorial/html/connmgmt.html#d4e506
sf.setHostnameVerifier(SSLSocketFactory.STRICT_HOSTNAME_VERIFIER);
return sf;
} catch (Exception e) {
throw new AssertionError(e);
}
}
}
With this step, the custom HttpClient is created, which can be used for secure connections.
Read Other Important Resources
- How to Reduce Vulnerabilities & Online Malware Attacks on Android Devices
- Understanding WildCard SSL validation for the Android Platform
- Mobile Cloud Computing – The Future of Mobile Applications
- Enable Two-Factor Authentication – An All-in-One Guide
SSL Certificates for Android Apps

Secure Android Webstore through an SSL Certificate from the most popular SSL brands like RapidSSL, GeoTrust, Thawte, and Symantec.








