Stay Safe on Apache Web Server with Thawte SSL Certificates
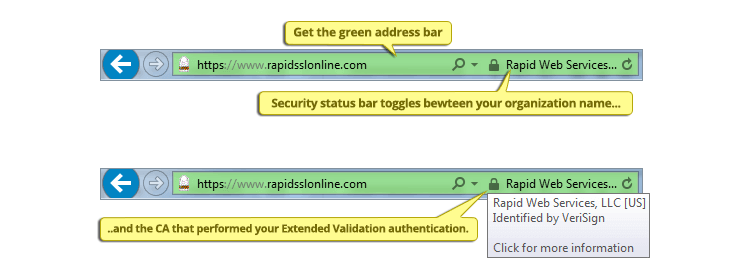
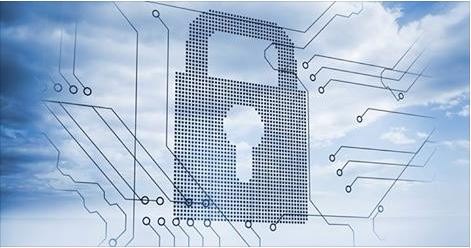
By using a Thawte secure sockets layer (SSL) digital certificate, organizations are able to directly implement SSL/TLS properly on the Apache server platform. Many users of encryption fail in one or more areas of the implementation, leading to embarrassment and financial losses for web hosting companies, application service providers, e-commerce shops and other online organizations. For the consumers violated by these failures, the financial losses might not compare to the loss of trust and perceived threat of identity theft. Thawte provides a higher level of trust by doing extended validation in issuance of digital certificates. This is clearly visible to users through the Thawte Trusted Site Seal and green address bar.
The old saying that a chain is only as strong as its weakest link definitely applies in the use of SSL certificates. In fact, SSL is practically useless when deployed with self-signed certificates, mixed port HTTP sites, unencrypted cookies or when encrypting at rates that cannot withstand brute force attacks. Thawte serves any organization seeking reliable implementations of digital certificates on Apache. These certificates operate smoothly with all aspects of Apache, including virtual hosts, OpenSSL, ModSSL and Apache-SSL. By using Thawte SSL certificates with extended validation, visitors to an Apache host see that the certificate is valid and that “Thawte Inc [US]” provided the validation.
Securing any Apache server is a simple process. The server manager should install OpenSSL and ModSSL, Apache-SSL or any other library services that creates the interface between Apache and OpenSSL. Using the “openssl” application from the command prompt, the server manager should generate the “private” key that is used to make the official certificate signing request (CSR) to Thawte.
Common “openssl” command formats and options are available elsewhere; the server manager should not experiment with the CSR request process or “play around” with actual signings. There are multiple methods to test certificates, including creating self-signed test certificates that are signed by self-generated private keys. These methods for testing are fully compliant with X.509, but they have no purpose for authentication or encryption beyond the test and install process. Proper testing should occur in cases where the server managers or implementation team are inexperienced with the full process.
To conclude the actual implementation on the Apache server, the certificate is downloaded and installed by pasting into the proper server location. Thawte recommends using the name “www.domain.com.crt” for consistency. If the server’s “httpd.conf” is missing the SSL Certificate File and SSL Certificate Key File directives, the server manager or implementation team should add them appropriately.
The implementation team should validate the success of the SSL implementation on the Apache server by connecting through multiple browsers and as many points of connection into the internet cloud as expected. Thawte recommends that troubleshooters begin with the Apache SSL FAQs at Thawte’s website.






 (5 votes, average: 4.00 out of 5, rated)
(5 votes, average: 4.00 out of 5, rated)